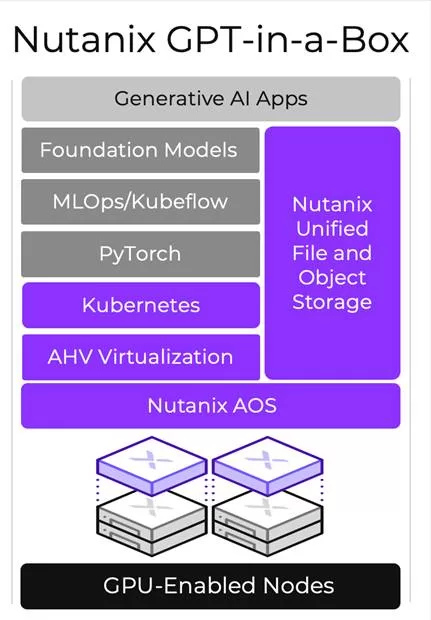
In efforts to advance hybrid cloud capabilities and empower Singapore’s workforce with essential tech skills, Nutanix and ST Engineering have joined forces through a two-year Memorandum of Understanding (MoU).
Hybrid cloud technology is a way of using both public and private cloud services together. It allows organisations to store some data in a public cloud while keeping other sensitive data in a private cloud.
Nutanix, a multi-cloud computing company, and ST Engineering, a technology and engineering group, have outlined their commitment to several key areas. Among these areas are:
Develop cutting-edge hybrid cloud technologies
Firstly, the partnership aims to develop cutting-edge hybrid cloud technologies tailored to the specific operational needs of organisations.
This collaborative effort combines public and private clouds to store data and manage multiple cloud services. It does this while prioritising strong security measures for data protection.
Additionally, the partnership aims to create a user-friendly cloud management portal. This portal will simplify multi-cloud management for businesses and enhance their control over cloud resources.
Cultivate a future-ready workforce through a curated training curriculum
Secondly, ST Engineering and Nutanix plan to cultivate a future-ready workforce through a curated training curriculum focused on hybrid cloud technology. This educational initiative will target higher learning institutions, equipping students with the skills necessary to excel in cloud-centric environments.
The training curriculum will include various cloud-related domains, aligning with government-wide efforts to build deep tech skills, particularly in cloud computing.
In conclusion, this collaboration between Nutanix and ST Engineering represents an important step towards enhancing Singapore’s hybrid cloud capabilities. It should also ensure that the workforce is well-prepared to navigate the evolving technology landscape.