Digitization and AI deployment in the manufacturing space doesn’t need to revolutionary, it can be evolutionary according to Red Hat’s Kelly Switt.
Beyond Moore’s Law: Micron’s Pursuit of Sustainable Innovation
Micron is leading the industry not just with technology, its leading the way when it comes to creating an impact with sustainability. We sat down with Mr Amarjit Sandhu to learn more.
Sustainability for the AI Future Needs to Start with Data Centres
Data centres are going to be the backbone of a digitised future. As such, their sustainability is becoming an increasingly important factor for companies.
Strengthening Core Infrastructure with Proactive Measures and Monitoring
As more cities move towards becoming Smart Cities, the need to strengthen core digital infrastructure requires a shift from being reactive to proactive.
Creating Teams That Keep Tech Companies Ahead of the Curve – A Sit Down with Suthen Thomas Paradatheth, Chief Technology Officer at Grab
techENT sits down with Suthen Thomas Paradatheth to talk about the innovation and tech at Grab and the driving force behind it.
Recognizing Third-Party Risks & Addressing the Gaps with Identity-Based Security
FSIs and other organisations are facing increased exposure when it comes to third-party risk – an aspect of cybersecurity that has gone unnoticed.
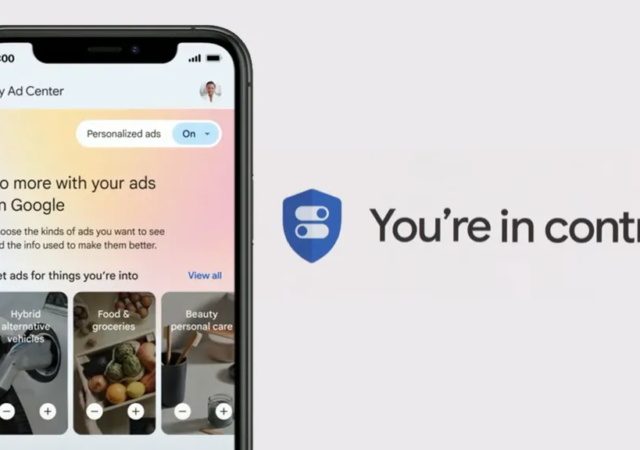
Interview: Getting to Know Google’s New My Ads Center
techENT sits down with a Google Spokesperson to take a deep dive into My Ad Center and how it will impact user and advertiser experience.
Tech & Tonic Episode 2 feat. Vernon Chan – Pre-Order, Cash, or Installment? Oh, Use Protection Everyone!
Episode two of Tech & Tonic we have a featured guest who is none other than Vernon Chan! He will be joining us today to talk about a few key aspects of how the local tech market is, to…