Simple, hyper-efficient compliance solution by Blackpoint adds to cybersecurity ecosystem ELLICOTT CITY, Md., June 16, 2021 — Blackpoint Cyber, a leading technology-focused cybersecurity company, has announced the launch of their newest MDR add-on solution, Blackpoint LogIC (Logging with Integrated Compliance). Blackpoint Cyber launches Blackpoint LogIC, a simple…
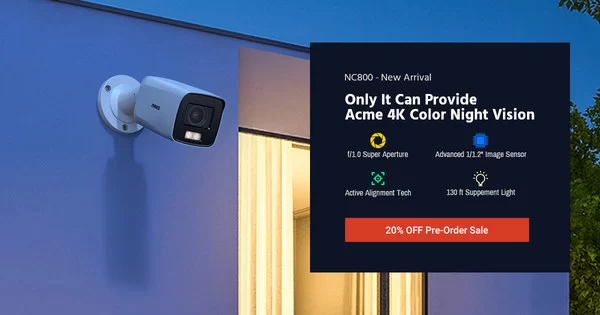
ANNKE Introduces New NightChroma™ NC800 PoE IP Camera Featuring Breakthrough 4K Ultra HD Color Night Vision, f/1.0 Super Aperture, and AI Processing Power
HONG KONG, June 8, 2021 — ANNKE, created for security, today launched NightChromaTM NC800, the world’s most powerful & advanced IP camera ever, pushing the limits of what’s possible in video surveillance. The ANNKE-designed 1/1.2” sensor, f/1.0 super aperture, and other high-end technologies deliver a massive leap in night vision clarity…
QueryPie, the data governance platform, becomes Okta Integration Network partner in Korea
SEOUL, South Korea, June 4, 2021 — QueryPie, the data governance platform, now has verified integration with Okta and is available through the Okta Integration Network (OIN), for the first time in Korea. By enabling technical partnerships in addition to its affiliation with Okta’s OIN Network, QueryPie intends to highlight more…
Contrast Security’s State of Application Security in Financial Services Report Finds 75% of Application Security Budgets Are Rising in 2021 Due to Frequent Application Attacks
98% of financial services respondents admit they have experienced at least three successful application exploits in the last 12 months that have caused an operational disruption and/or a data breach leading to the increase in application security budgets LOS ALTOS, Calif., May 27, 2021 — Contrast Security, a leader in…
Airports to be Fastest-growing Critical Infrastructure Sector to Invest in Cybersecurity by 2030
The global critical infrastructure cybersecurity market is estimated to reach $24.22 billion by 2030, finds Frost & Sullivan SANTA CLARA, Calif., May 24, 2021 — Frost & Sullivan’s recent analysis finds that while corporate and consumer businesses remain popular marks for cyberattacks, critical infrastructure facilities have become increasingly viable threat…
CyberPurify makes the world’s first online content filtering in realtime
SAN JOSE, Calif., May 22, 2021 — CyberPurify, a startup specializing in using Machine Learning to identify harmful content, has just launched a free solution called CyberPurify Kids to help parents around the globe create a safe online environment for their kids in just a few clicks. …
Contrast Security Joins Cloud Native Computing Foundation and Linux Foundation to Drive Security Best Practices Around Cloud Native Architectures and Open Source Software
Contrast furthers commitment to empower organizations to rapidly build and run scalable applications in modern, dynamic environments with security integrity LOS ALTOS, Calif., May 19, 2021 — Contrast Security, a leader in modernizing application security, today announced that it has joined the Cloud Native Computing Foundation (CNCF) and Linux Foundation as a silver…
TXOne Networks Named Winner of the Coveted Global InfoSec Awards during RSA Conference 2021
TXOne Networks wins categories “Most Innovative in Critical Infrastructure Protection” and “Editor’s Choice in ICS/SCADA Security” in 9th Annual Global InfoSec Awards at #RSAC 2021 SAN FRANCISCO and TAIPEI, May 18, 2021 — TXOne Networks, a leading provider in OT Security solutions, is proud to announce that they have won the…
RevBits® Named Winner of the Coveted Global InfoSec Awards during RSA Conference 2021
Cybersecurity Solutions provider RevBits Wins Multiple Awards in the 9th Annual Global InfoSec Awards at #RSAC 2021 MINEOLA, N.Y., May 17, 2021 — RevBits is proud to announce that it was the winner of the following award(s) from Cyber Defense Magazine (CDM), the industry’s leading electronic information security magazine: RevBits recognized for innovation across three of its cybersecurity solution…
Skybox Security Wins Best Vulnerability Management Solution
SC Awards honor the best in U.S. cybersecurity SAN JOSE, Calif., May 6, 2021 — Skybox Security, a global leader in security posture management, today announced it won Best Vulnerability Management Solution at the 2021 SC Awards. Honoring the best in U.S. cybersecurity, the annual…