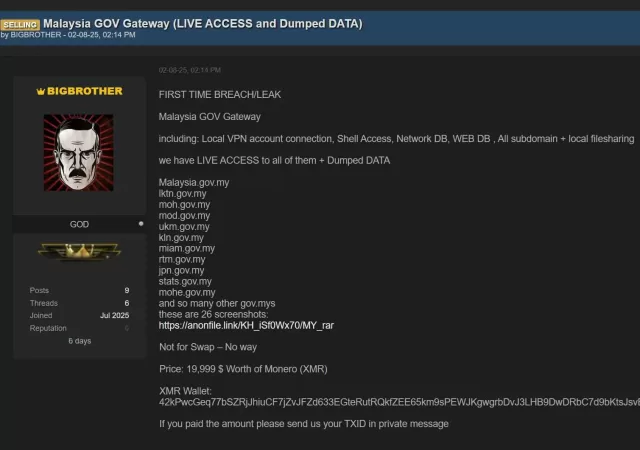
A hacker has surfaced claiming to have compromised a number of Malaysian Government websites collecting sensitive information.
ESET reports cyberthreats to Ukraine by Russian APT
Cybersecurity company ESET released its latest APT Activity Report, shedding light on coordinated threats to cybersecurity across the globe for 2022. Advanced Persistent Threats or APT, are broadly defined as targeted cyberattacks by either a single person or a coordinated…
How ethical hacking can improve your security posture
The current landscape of cyber security has changed dramatically. Protection through conventional methods may not be too effective.