Companies continually need to be at the forefront. With the emergence of edge computing and 5G, the need for collaborative innovation is even more prevalent.
Vigilance is Crucial for Businesses in Dealing with Modern Malware
With ransomware evolving so quickly, businesses must be ever vigilant or risk losing their reputation and assets.
Resilience in the wake of 2020: Red Hat’s path in 2021
Looking forward from a year tainted by a global pandemic, Red Hat looks to the future of Open Source and digitization in building business resilience.
AWS Committed to Accelerating Malaysia’s Digital Transformation
Amazon Web Services (AWS) has been a part of Malaysia’s digital transformation journey since 2015 when we established our presence in the country with a local marketing entity, AWS Malaysia Sdn. Bhd. The announcement by the Malaysian Government outlining the…
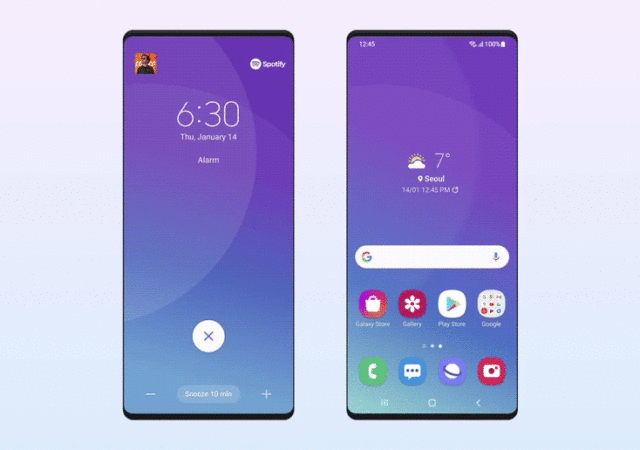
A Deep Dive into One UI’s Design
The designers at Samsung give us a look into the ethos of One UI’s latest update and how it will shape the user experience for Galaxy Devices.
We’re in the Golden Age of Machine Learning, Tomorrow it will be Ubiquitous – Four Things We Need to Do Now
With A.I. and Machine Learning becoming more mainstream, it’s time to look to the future and how companies, their leadership and education can play a role.
Beyond the Now: Thrive in 2021 with These Five Trends
Red Hat weighs in on the emerging trends that will define the technology landscape and help organizations thrive in 2021.
Mastering Modern Photography with your Smartphone
Photographs are the mighty connectors of the world today. You may not master any other language aside from your native tongue, but you know this much is true – a picture is worth a thousand words and having the right…
Four Steps to Accelerate Your Machine Learning Journey
Machine Learning is all the buzz right now, particularly with the current state of flux businesses are in. But where do we start?